Type of Authentication - JWT Authentication
As we already discussed rest of the authentication types in our previous video tutorials, JWT based authentication is best among all. It is world famous and used in almost all modern web/distributed applications. In this video tutorial 0010-3 What is JWT Based Authentication we will discuss about JWT authentication in detail.
JWT lets you store encrypted information in verifiable tokens. These tokens are compact and self-contained encoded JSON objects that hold vital information which is transferred between client and server. JWTs have three parts:
Header: First part holds the hashing algorithm.
Payload: The second part which is payload consists of authentication data.
Signature: Third part is Signature which is created by signing the header and payload using the hashing algorithm and secret key. This signing process is what verifies the token.
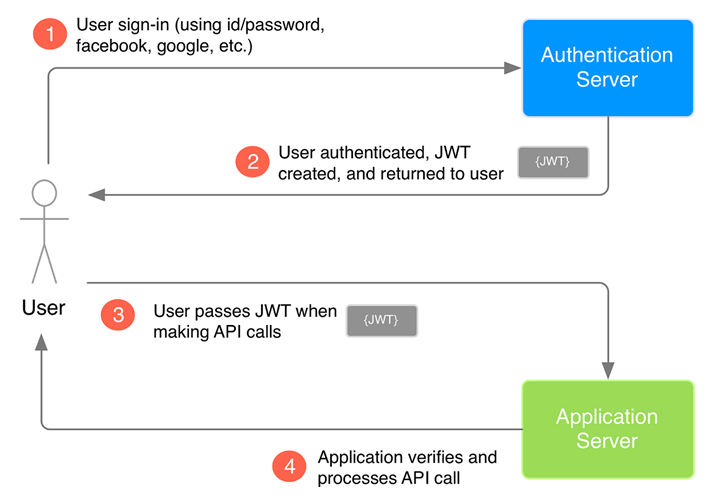
Below snapshot from our video session shows diagrammatical explanation of JWT authentication process.

In our subsequent video sessions, we will deep dive into JWT working process and try to understand how it overcomes shortcomings of other authentication types and what makes it best among all.




Comments